In today’s digital landscape, ensuring the security of applications is paramount. The complexity and variety of threats necessitate a multifaceted approach to security testing. This comprehensive guide aims to demystify SAST, DAST, IAST, and RASP, explaining each method’s unique features, benefits, and applications. By understanding these tools, organizations can better protect their applications from vulnerabilities and attacks.
What Is SAST, DAST, IAST, and RASP?
Before diving in, let’s define SAST, DAST, IAST, RASP, and their roles in application security.
Understanding SAST (Static Application Security Testing)
Static Application Security Testing (SAST) is a method used to analyze an application’s source code, bytecode, or binary code for vulnerabilities. This approach examines the code without executing the application, allowing for the detection of issues early in the development lifecycle.
Key Characteristics of SAST
- SAST tools analyze the codebase to find vulnerabilities like buffer overflows, SQL injection, and XSS.
- Integrating SAST into development allows developers to detect and fix vulnerabilities before application deployment.
- Comprehensive Review: SAST provides a deep dive into the code, offering a thorough analysis of potential security issues.
Advantages of SAST
- Early vulnerability detection during development helps mitigate risks before the application is deploye.
- Detailed Insights: SAST tools provide detailed information about vulnerabilities, including their location and nature.
- Continuous Integration: SAST can be integrated into CI/CD pipelines, ensuring ongoing security checks throughout the development process.
Exploring DAST (Dynamic Application Security Testing)
The demystifying sast dast iast and rasp Dynamic Application Security Testing (DAST) evaluates an application’s security while it’s running, testing for vulnerabilities in its live environment, unlike SAST which examines code.
Key Characteristics of DAST
- DAST tools simulate real-world attacks to identify issues like authentication flaws, session management problems, and input validation vulnerabilities.
- No Code Access: DAST does not require access to the source code, making it suitable for testing third-party applications or applications where the code is not available.
- Real-World Simulation: By interacting with the application as an external user would, DAST provides insights into how an attacker might exploit vulnerabilities.
Advantages of DAST
- Real-World Testing: Simulates attacks to find vulnerabilities that can be exploited in a live environment.
- No Source Code Needed: Tests the application from an external perspective, making it versatile for various testing scenarios.
- Comprehensive Coverage: Identifies runtime issues and configuration problems that static analysis might miss.
Delving into IAST (Interactive Application Security Testing)
IAST blends SAST and DAST, analyzing applications during runtime to provide detailed insights by correlating code behavior and runtime data.
Key Characteristics of IAST
- IAST tools integrate with application servers for static and dynamic analysis, providing a comprehensive vulnerability assessment.
- Contextual Awareness: Provides detailed insights by examining the application’s behavior in real-time, offering a deeper understanding of vulnerabilities.
- Continuous Monitoring: IAST tools offer ongoing security assessments as the application is running, providing up-to-date information on potential issues.
Advantages of IAST
- Detailed Analysis: Combines static and dynamic analysis to provide accurate and context-rich vulnerability information.
- Reduced False Positives: By correlating runtime data with code analysis, IAST tools reduce the number of false positives.
- Real-Time Insights: Offers continuous monitoring and assessment during application execution, ensuring current security status.
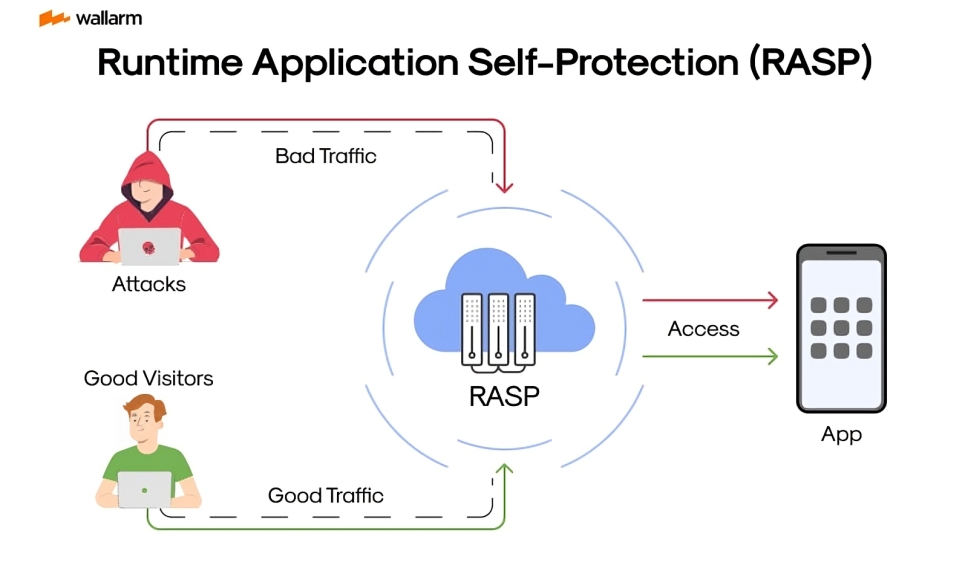
Understanding RASP (Runtime Application Self-Protection)
The demystifying sast dast iast and rasp RASP is embedded within applications to protect them during runtime, actively defending against attacks unlike SAST, DAST, and IAST
Key Characteristics of RASP
- Real-Time Defense: RASP tools detect and block attacks in real-time, providing immediate protection against exploitation.
- Application-Specific: Tailors security measures to the specific application, offering customized protection based on its unique characteristics.
- Minimal Performance Impact: Operates within the application with minimal
- RASP provides protection with minimal performance overhead compared to traditional security solutions.
Advantages of RASP
- Active Protection: Provides real-time defense against attacks, reducing the risk of exploitation.
- Customized Security: Offers protection tailored to the specific application, enhancing security measures.
- Low Overhead: Integrates with the application with minimal impact on performance.
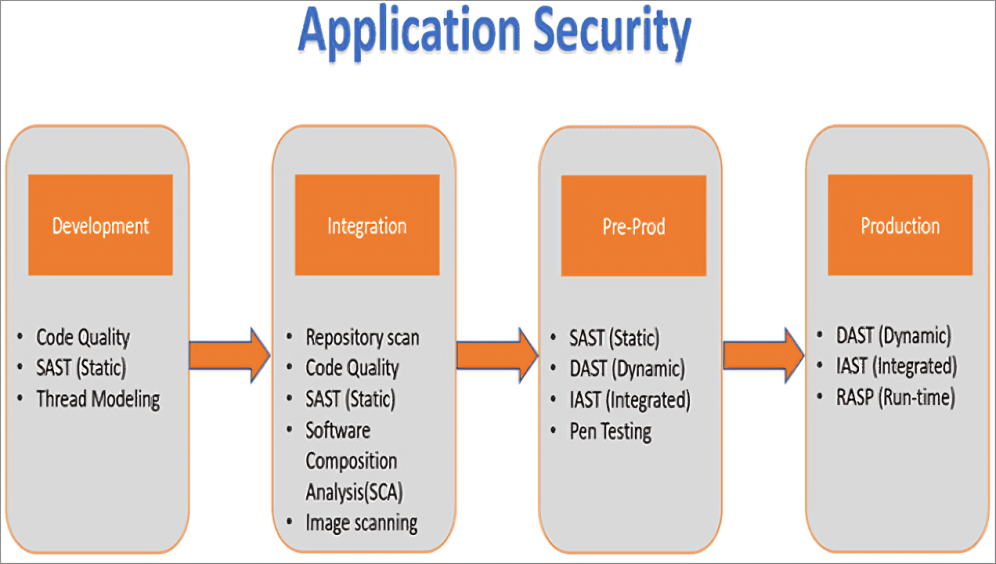
Comparing SAST, DAST, IAST, and RASP
To effectively utilize SAST, DAST, IAST, and RASP, understanding their differences and complementary roles is essential. Here’s a comparison to help, The demystifying sast dast iast and rasp clarify how these methods can work together to enhance application security.
SAST vs. DAST
- SAST is ideal for early development, identifying vulnerabilities before deployment with deep codebase analysis and source access.
- DAST is suitable for testing applications in a live environment, where it simulates real-world attacks. It does not require code access and focuses on runtime issues, making it valuable for identifying vulnerabilities that occur in the application’s operational state.
IAST vs. RASP
- IAST offers a hybrid approach by combining static and dynamic analysis. It offers detailed insights into vulnerabilities by analyzing the application’s behavior during runtime. It’s effective for ongoing assessments and provides context-rich information.
- RASP focuses on real-time protection by actively defending against attacks as they happen. It is application-specific and operates with minimal performance impact, offering immediate defense but not replacing the need for pre-deployment testing.
How to Implement SAST, DAST, IAST, and RASP in Your Security Strategy
Implementing SAST, DAST, IAST, and RASP effectively requires careful planning and integration into your security strategy. Here’s how to approach each method:
Implementings SAST
- Integrate SAST tools into your CI/CD pipeline to ensure continuous security checks throughout the development process.
- Train Developers: Educate your development team on how to use SAST tools and interpret the results to address vulnerabilities efficiently.
- Review Regularly: Conduct regular reviews of SAST results to identify and address vulnerabilities early in the development process.
Implementings DAST
- Schedule Regular Scans: Perform DAST scans periodically to identify vulnerabilities in your live applications.
- Simulate Real-World Attacks: Use DAST tools to simulate various attack scenarios and evaluate how your application responds.
- Analyze Results: Review DAST results to identify runtime vulnerabilities and configure your application to address them.
Implementing IAST
- Integrate with Application Server: Deploy IAST tools within your application server to enable continuous security assessments.
- Monitor in Real-Time: Use IAST to continuously monitor application behavior and provide real-time insights into vulnerabilities.
- Correlate Data: Analyze the correlation between static code analysis and runtime data to obtain accurate vulnerability information.
Implementing RASP
- Embed RASP technology in your application to ensure real-time protection against threats during runtime.
- Customize Protection: Configure RASP settings based on the specific needs and characteristics of your application.
- Monitor and Update: Continuously monitor the effectiveness of RASP and update it as necessary to address emerging threats.
FAQs
What is SAST?
Static Application Security Testing (SAST) analyzes the source or binary code of an application to identify vulnerabilities without executing the application.It is useful for detecting security issues early during the development phase.
What is DAST?
Dynamic Application Security Testing (DAST) evaluates an application’s security in real-time by simulating real-world attacks. It identifies vulnerabilities that can be exploited in a live environment and does not require access to the source code.
What is IAST?
Interactive Application Security Testing (IAST) combines static and dynamic analysis for detailed vulnerability insights, reducing false positives and offering continuous monitoring.
What is RASP?
Runtime Application Self-Protection (RASPs) is a technology embedded within an application to provide real-time protection against attacks. It actively defends the application during runtime and offers customized security measures.
How do SAST, DAST, IAST, and RASP work together?
SAST, DAST, IAST, and RASPs complement each other by addressing different aspects of application security. SAST and DAST focus on identifying vulnerabilities, IAST provides detailed analysis, and RASPs offers real-time protection.
Conclusion
Demystifying SAST, DAST, IAST, and RASPs reveals how each method plays a vital role in ensuring comprehensive application security. By understanding their unique features and benefits, organizations can effectively integrate these tools into their security strategies. Whether you need early vulnerability detection, real-time protection, or comprehensive analysis, combining these approaches will help build a robust defense against potential threats. In the ever-evolving landscape of cybersecurity, leveraging SAST, DAST, IAST, and RASPs.